Home
About us Comments
Webmaster Links
Books To Read Movies
Archives Blog
Shop
Blogged by Brad
on 9/15/2005 @ 11:05am PT...Starship Troopers
* EXCLUSIVE! * A DIEBOLD INSIDER SPEAKS!
DIEB-THROAT : 'Diebold System One of Greatest Threats Democracy Has Ever
Known'
Identifies U.S. Homeland Security 'Cyber Alert' Prior to '04 Election Warning
Votes Can be 'Modified Remotely' via 'Undocumented Backdoor' in Central
Tabulator Software!
 In
exclusive stunning admissions to The
BRAD BLOG some 11 months after the 2004 Presidential Election, a
"Diebold Insider" is now finally speaking out for the first time about
the alarming security flaws within Diebold, Inc's electronic voting systems,
software and machinery. The source is acknowledging that the company's
"upper management" -- as well as "top government officials"
-- were keenly aware of the "undocumented backdoor" in Diebold's main
"GEM Central Tabulator" software well prior to the 2004 election. A
branch of the Federal Government even posted a security warning on the Internet.
In
exclusive stunning admissions to The
BRAD BLOG some 11 months after the 2004 Presidential Election, a
"Diebold Insider" is now finally speaking out for the first time about
the alarming security flaws within Diebold, Inc's electronic voting systems,
software and machinery. The source is acknowledging that the company's
"upper management" -- as well as "top government officials"
-- were keenly aware of the "undocumented backdoor" in Diebold's main
"GEM Central Tabulator" software well prior to the 2004 election. A
branch of the Federal Government even posted a security warning on the Internet.
Pointing to a
little-noticed "Cyber Security Alert" issued by the United States
Computer Emergency Readiness Team (US-CERT), a division of the U.S. Department
of Homeland Security, the source inside Diebold -- who "for the time
being" is requesting anonymity due to a continuing sensitive relationship
with the company -- is charging that Diebold's technicians, including at least
one of its lead programmers, knew about the security flaw and that the company
instructed them to keep quiet about it.
"Diebold threatened violators with immediate dismissal," the insider,
who we'll call DIEB-THROAT, explained recently to The
BRAD BLOG via email. "In 2005, after one newly hired member of
Diebold's technical staff pointed out the security flaw, he was criticized and
isolated."
In phone interviews, DIEB-THROAT confirmed that the matters were well known
within the company, but that a "culture of fear" had been developed to
assure that employees, including technicians, vendors and programmers kept those
issues to themselves.
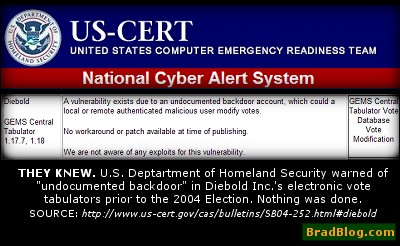
The "Cyber Security Alert" from US-CERT was issued in late August of
2004 and is still available online via the US-CERT
website. The alert warns that "A vulnerability exists due to an
undocumented backdoor account, which could [sic: allow] a local or remote
authenticated malicious user [sic: to] modify votes."
The alert, assessed to be of "MEDIUM" risk on the US-CERT security
bulletin, goes on to add that there is "No workaround or patch available at
time of publishing."
"Diebold's upper management was aware of access to the
voter file defect before the 2004 election - but did nothing to correct
it," the source explained.
A "MEDIUM" risk vulnerability cyber alert is described on the US-CERT
site as: "one that will allow an intruder immediate access to a system with
less than privileged access. Such vulnerability will allow the intruder the
opportunity to continue the attempt to gain privileged access. An example of
medium-risk vulnerability is a server configuration error that allows an
intruder to capture the password file."
DIEB-THROAT claims that, though the Federal Government knew about this
documented flaw, originally discovered and reported by BlackBoxVoting.org
in August of 2004, they did nothing about it.
"I believe that top Government officials had an understanding with top
Diebold officials to look the other way," the source explained,
"because Diebold was their ace in the hole."...
But even DIEB-THROAT -- who says "we were brainwashed" by the company
to believe such concerns about security were nonsense -- was surprised to learn
that an arm of the U.S. Department of Homeland Security was well aware of this
flaw, and concerned enough about it to issue a public alert prior to the
election last year.
"I was aware of the Diebold security flaw and had heard about the Homeland
Security Cyber Alert Threat Assessment website, so I went there and 'bingo,'
there it was in black and white," the source wrote. "It blew me away
because it showed that DHS, headed by a Cabinet level George Bush loyalist, was
very aware of the 'threat' of someone changing votes in the Diebold Central
Tabulator. The question is, why wasn't something done about it before the
election?"
The CEO of North Canton, Ohio-based Diebold, Inc., Walden O'Dell has been
oft-quoted for his 2003
Republican fund-raiser promise to help "Ohio deliver its electoral
votes to the president next year." O'Dell himself was a high-level contributor
to the Bush/Cheney '04 campaign as well as many other Republican causes.
"A very serious problem...one malicious person can change the outcome
of any Diebold election"
The voting company insider, who has also served as a spokesperson for the
company in various capacities over recent years, admits that the "real
danger" of this security vulnerability could have easily been exploited by
a malicious user or an insider through remote access.
"I have seen these systems connected to phone lines dozens of times with
users gaining remote access," said DIEB-THROAT. "What I think we have
here is a very serious problem. Remote access using phone lines eliminates any
need for a conspiracy of hundreds to alter the outcome of an election. Diebold
has held onto this theory [publicly] for years, but Diebold has lied and has put
national elections at risk. Remote access using this backdoor means that one
malicious person can change the outcome of any Diebold election."
The ability to connect to the system remotely by phone lines and the apparent
lack of interest by Diebold to correct the serious security issue in a timely
manner -- or at all -- would seem to be at odds with at least one of their Press
Releases touting their voting hardware and software.
In an October 31, 2003 Press Release as part of a publicity blitz to
"sell" the new voting machines to the voters in the state of Maryland,
Diebold Election Systems President Thomas W. Swidarski is quoted as follows in a
section titled "Security Is Key":
Diebold has fine-tuned its computerized system so that it meets stringent
security requirements. “We have independent verification that the Diebold
voting system provides an unprecedented level of election security. This is
crucial to maintaining the integrity of the entire voting process,”
Swidarski added.
Attempts by The BRAD BLOG
to get comment from Swidarski were passed to one of the Vice-Presidents at
Diebold who has not returned our voice mail message.
We did, however, hear back from Diebold Spokesperson David Bear of the PR firm
Public Strategies. He was referred to us by several different Diebold offices as
"the man to discuss voting machine issues with."
Bear claimed to have never heard of the Cyber Alert issued by US-CERT and when
told of it, refused to acknowledge it as anything more than "an unverified
allegation."
"One of the greatest threats our democracy has ever known"
Our source expressed emphatically that future democratic elections in the United
States are at stake and feels that the problem will not be corrected until
Congressional action forces the company to do so.
"In my opinion Diebold's election system is one of the greatest threats our
democracy has ever known, and the only way this will be exposed is with a
Congressional investigation with subpoenas of not just Diebold officials but
Diebold technicians."
If our experience in discussing the matter with Bear, the man Diebold referred
us to for all matters concerning voting machines, is any indication, then DIEB-THROAT
may be correct. Even a Cyber Alert Bulletin issued by an official arm of the
U.S. Department of Homeland Security more than a year ago was not enough to
phase Diebold. At least not enough to even inform their public spokesperson
about the matter, apparently.
"I don't know anything about it," Bear claimed when we asked about the
Cyber Alert, and he refused to acknowledge there were anysecurity
concerns about Diebold's Voting Machines or its GEMS Central Tabulator software.
Over and over, by rote, he repeated in response to our questions: "The GEMS
software has been used in hundreds of elections and there's never been a
security issue."
Bear says that "Diebold machines have never lost a single vote," but
beyond that could not speak to the vulnerability issue since, he said, "I
don't know what vulnerability they're referencing."
We sent the
link to the US-CERT Cyber Alert to Bear, but have not yet heard back from
about it. He did, however, send us a copy of the well-worn Caltech/Massachusetts
Institute of Technology report [PDF] analyzing the 2004 Presidential
Election which, Bear pointed out in his Email, "concludes that the most
improvement [in vote-counting and integrity over 2000] occurred when
counties/states changed to touch screen systems."
DIEB-THROAT was taken aback, but not wholly surprised, when we shared the
comments from Bear denying knowledge of the "backdoor" security
vulnerability in the GEMS software and his contention that there was nothing
more than "allegations."
The vulnerability, and the ability to "manipulate votes" occurs
because the GEMS software uses the public Microsoft Access database software to
store vote totals in a separate data file. And, as DIEB-THROAT explained, Access
is "full of holes. There are so many ways to get into it."
Because GEMS uses the Access database, "you can enter and manipulate the
file without even entering into GEMS," our source said in response ot
Bear's denials.
"GEMS sits on top of this database and it pretty much feeds information
down to the database from GEMS. It's almost like you're on the first floor of
your house and all of your operating equipment is in the basement so that
anything that happens on the first floor ends up downstairs. Well, downstairs
has a wide open door to it. So we're dumping all the votes downstairs and that's
wide open to the rest of the computer system."
"A culture of fear"
In trying to understand why the U.S. Homeland Security Department's Cyber Alert
didn't force Diebold to make fixes, patches or corrections quickly available for
their software prior to -- or even since -- the '04 election, DIEB-THROAT
repeated over and over that Diebold was simply "not concerned about
security".
"They don't have security solutions. They don't want them...They leave
security policy issues up to the states. They've known about this for some time.
They don't really care," the source said, comparing the security flaw to
"leaving the front door at Fort Knox open." It's just "blatant
sloppiness and they don't care."
The versions of the GEMS Central Tabulation software listed on the US-CERT site
are 1.17.7 and 1.18 and DIEB-THROAT says the same versions of the same software
are still in use by States around the country and haven't had any fixes or
patches applied to correct the problem.
Diebold spokesman, Bear, was unable to confirm whether or not Diebold had
updated its GEMS software in any way since the US-CERT Cyber Alert was released
telling us only that "There's different versions of the software for
different needs" and that he didn't know if patches, fixes or corrections
were ever released by the company.
"There's always an evolution," Bear said. "Before any software
can be used it's federally qualified and then certified by the states...Where
different versions are running, I just don't know."
"They're still at that same version number," DIEB-THROAT said. "A
lot of our customers still have it and there's not been any patch....They really
don't care about this sort of thing. They really don't. People may find it hard
to believe...in other words [the company says] 'we'll give you a machine to vote
on and the rest is up to you."
"This is a very profit motivated company," the source continued,
"they don't care what happens after the sale. Once they have the contract
they've got the customer tied up pretty good."
Initially DIEB-THROAT claims to have been "brainwashed" by the
pervasive "company line" at Diebold, that all of the talk about
security concerns and the possibility that someone could hack the vote was the
talk of "conspiracy theorists". Apparently that was -- and is still is
-- "the company line." But after one of Diebold's head technicians who
works out of their McKinney, Texas facility confirmed the gaping security hole
in the software to our source, it was understood that these concerns were for
real.
"Up until his confirmation, I had heard it through the grapevine, as
rumors and such, but he confirmed it for me. The lead technician who worked on
the software, who has a Phd in mathematics and so forth, was saying that 'this
problem exists!'"
So why hasn't that technician, or anyone else from within the company spoken out
until now?
"This is a culture of fear. Really. Only because we were good friends did
[the head technician] confide in me that these were problems that needed
to be fixed," DIEB-THROAT said.
"They all knew..."
In regards to possible remote access to the GEMS Central Tabulator by modem via
phone lines, a way that hackers could easily and simply change the vote total
information in the Access database, Diebold's official spokesman seemed to be
similarly in denial even today.
When we asked Bear whether or not the Central Tabulator is still accessible via
modem in their machines, he first denied that it's even possible, telling us
"the Central Tabulator isn't accessable via modem."
When we pressed about whether or not there are still modem capabilities in the
machines and software they sell, Bear admitted, "There is a modem
capability, but it's up to a jurisdiction whether they wish to use it or not...I
don't know of any jurisdiction that does that."
"Oh, boy. Such lies," DIEB-THROAT said in response. "There are
several jurisdications that use [the modem capabilities] in the
machines...Probably one of the most robust users of modems is Prince Georges
County in Maryland. They've used it in every election. I believe they started in
2000. And Baltimore County used them in the November election in 2004. Fulton
County and Dekalb County in Georgia may have used them in 2004 as well."
While we were unable to hear back in response to messages left with Election
Officials at several of those offices prior to the publication of this article,
a review of "Lessons Learned" after the November 2004 Election
conducted by the Maryland state Board of Elections obtained by The
BRAD BLOG, confirms that modems were used to access the GEMS Central
Tabulator to send in information from precincts on Election Night.
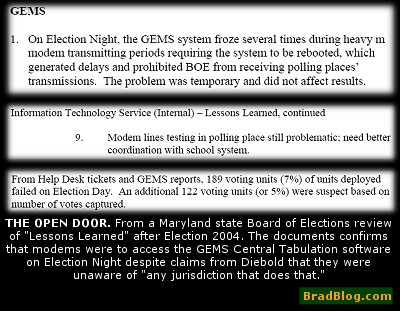
We are still reviewing the complete document, but amongst the findings in the
report is that "the GEMS system froze several times during heavy modem
transmitting periods requiring the system to be rebooted, which generated delays
and prohibited BOE from receiving polling places' transmissions."
As well, the report concludes, "Modem lines testing in polling place still
problematic; need better coordination with school system."
It also says that "7% of voting units deployed failed on Election Day"
and that an additional 5% "were suspect based on the number of votes
captured." The BRAD BLOG hopes to
have a follow-up article in the coming days which looks in more detail at the
full Maryland state Board of Elections report and the alarming rate of failure
for Diebold Touch-Screen voting machines.
When we asked our source if they had any evidence to show
that the security flaw described by the U.S. Dept. of Homeland Security was
actually exploited in the 2004 election, DIEB-THROAT told us only:
"I wouldn't say I have evidence that it was exploited....only that it was known.
To the feds, to state officials and to Diebold. They all knew. In spite of the
gap they moved forward as normal...As if it didn't exist."
Home
About us Comments
Webmaster Links
Books To Read Movies
Archives Blog
Shop
 In
exclusive stunning admissions to The
BRAD BLOG some 11 months after the 2004 Presidential Election, a
"Diebold Insider" is now finally speaking out for the first time about
the alarming security flaws within Diebold, Inc's electronic voting systems,
software and machinery. The source is acknowledging that the company's
"upper management" -- as well as "top government officials"
-- were keenly aware of the "undocumented backdoor" in Diebold's main
"GEM Central Tabulator" software well prior to the 2004 election. A
branch of the Federal Government even posted a security warning on the Internet.
In
exclusive stunning admissions to The
BRAD BLOG some 11 months after the 2004 Presidential Election, a
"Diebold Insider" is now finally speaking out for the first time about
the alarming security flaws within Diebold, Inc's electronic voting systems,
software and machinery. The source is acknowledging that the company's
"upper management" -- as well as "top government officials"
-- were keenly aware of the "undocumented backdoor" in Diebold's main
"GEM Central Tabulator" software well prior to the 2004 election. A
branch of the Federal Government even posted a security warning on the Internet.